Apple Copland Reference Documentation
The Copland project was Apple’s ill-fated attempt in the mid 1990s to replace the aging classic Mac OS with a more modern operating system that had a microkernel, virtual memory and preemptive multitasking. Information on Copland is scarce, therefore I have compiled 20 hard to find Copland reference documents, as well as the 359 page book “Mac OS 8 Revealed”.
Readable and Maintainable Bitfields in C
Bitfields are very common in low level C programming. You can use them for efficient storage of a data structure with lots of flags, or to pass a set of flags between functions. Let us look at the different ways of doing this.
A Lot of Security
Stamp Vending Machine DoS
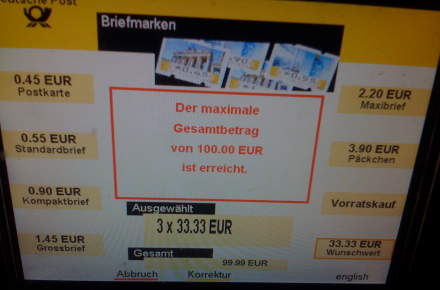
It makes sense for a stamp vending machine to have some limits and not print any amount of stamps or stamps of any value. The vending machines from the Deutsche Post are a little weird though:
Feed in Rogue Signal Here

Sometimes it makes sense to label a surveillance camera.
