64'er Magazin – mit 40 Jahren Verzögerung jetzt monatlich im Web
Zum 40jährigen Jubiläum des 64’er Magazins präsentieren wir das Kunstprojekt www.64er-magazin.de: eine Website, die so tut, als wäre 1984. Exakt 40 Jahre nach der ursprünglichen Veröffentlichung erscheint hier jeden Monat eine neue Ausgabe:
The Commodore AUTOMODEM (Model 1650)
The Commodore VICMODEM (Model 1600)
The Commodore 1600, also known as the “VICMODEM”, is Commodore’s very first modem (1982): It supports 300 baud duplex connections, and is connected to an existing telephone’s handset connector instead of the phone line. This kept the price down, but required the user to dial manually through the phone.
Ultimate Commodore Charset / PETSCII / Keyboard Reference
Another addition to the The Ultimate C64 Reference: We’re adding character sets, PETSCII codes and keyboard layouts – supporting eight different Commodore computers.
Commodore Peripheral Bus: Part 4: Standard Serial
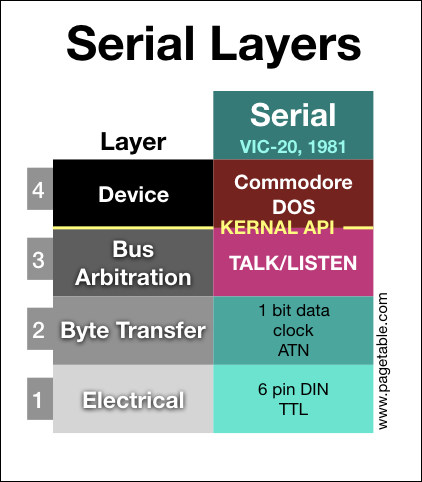
In the series about the variants of the Commodore Peripheral Bus family, this article covers the lowest two layers (electrical and byte transfer) of the “Standard Serial” bus as found on the VIC-20/C64 as the main bus, but also supported by all other Commodore home computers.


