The Ultimate Commodore 1541 Disk Drive Talk [video]
This is the video recording of “The Ultimate Commodore 1541 Disk Drive Talk” at VCF West 2021. As always, if you think it’s too fast, try watching it at 0.75x speed!
Some Assembly Required
This is the video recording of “The Ultimate Commodore 1541 Disk Drive Talk” at VCF West 2021. As always, if you think it’s too fast, try watching it at 0.75x speed!

After

This post is about an upcoming talk in German.
In the series about the internals of the geoWrite WYSIWYG text editor for the C64, this article discusses the geoWrite copy protection.
We are presenting the (to our knowledge) first full-featured open source library for 65c02 CPUs for accessing FAT32 formatted disks.
Update 2022: Web MiniDisc Pro can access NetMD devices through the browser and can also download protected files!
We have previously visualized the physical layout of C64/1541 disks. In order to understand the encoding and potential read errors, it is more useful to visualize the disks sector-by-sector.
There have been a few new interesting additions to the Commodore Source Code repository, including:
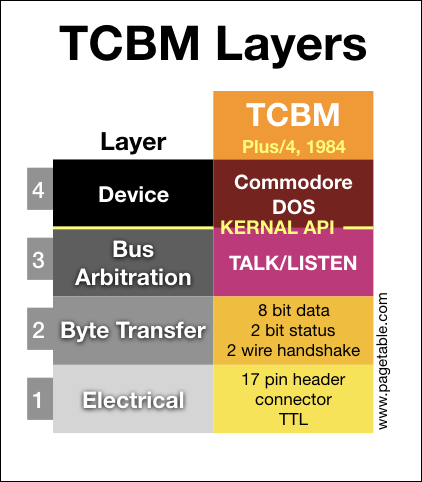
In the series about the variants of the Commodore Peripheral Bus family, this article covers the lowest two layers (electrical and byte transfer) of the “TCBM” bus as found on the TED series computers: the C16, C116 and the Plus/4.
After previously dissecting the firmware of alternate C64 disk drives, let’s now look at the hardware of one: This is the Blue Chip BCD/5.25.
extract-adf is a tool for recovering files from broken Amiga OFS filesystem images. It can reconstruct directory hierarchies even for files that don’t have directory entries.
Commodore 64 disk drives were usually connected through the slow serial bus. This article shows some hi-res photos of the Commodore “IEEE-488 cartridge”, which made the faster PET drives available for the C64.
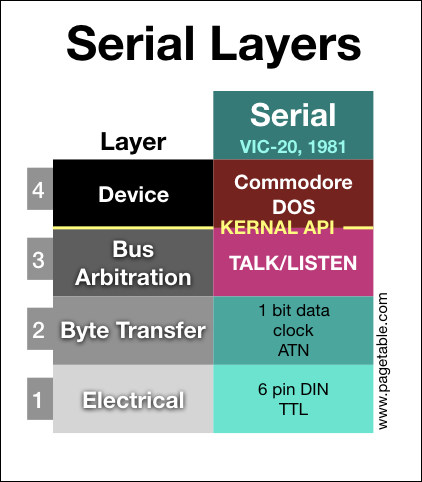
In the series about the variants of the Commodore Peripheral Bus family, this article covers the lowest two layers (electrical and byte transfer) of the “Standard Serial” bus as found on the VIC-20/C64 as the main bus, but also supported by all other Commodore home computers.
I have previously analyzed the ROM images of some third party disk drives for the Commodore 64: The result was that most of them were just using the original binaries with some obfuscation, and some with some added features. This time, let’s look at another drive, the “Technica”, which is a little special in this regard.
I have this pile of broken GEOS disks that were sent in for replacements. In two previous articles (1, 2), I explored the reasons why the disks broke. Now let’s be constructive: Can we reconstruct the original bits by combining the correct parts? This article shows how it is possible with the help of a small tool that combines the good parts of several broken disk images.

I happened to come across 50 original German GEOS 2.0 disks that were broken and sent in for replacement. In the first part, I covered the disks that were broken probably due to user error. Now let’s look at the read errors on the remaining disks. As it turns out, there might be a bug in GEOS that caused the boot disks to break!