Commodore's Assemblers: Part 4: HCD65
In the series about the assemblers Commodore used for developing the ROMs of their 8-bit computers, this article covers the 1987 “HCD65” assembler that ran on the C128.
Commodore's Assemblers: Part 3: BSO CY6502
In the series about the assemblers Commodore used for developing the ROMs of their 8-bit computers, this article covers the 1984 “Boston Systems Office” (BSO) cross-assembler running on VAX/VMS.
Commodore's Assemblers: Part 2: MOS Resident Assembler
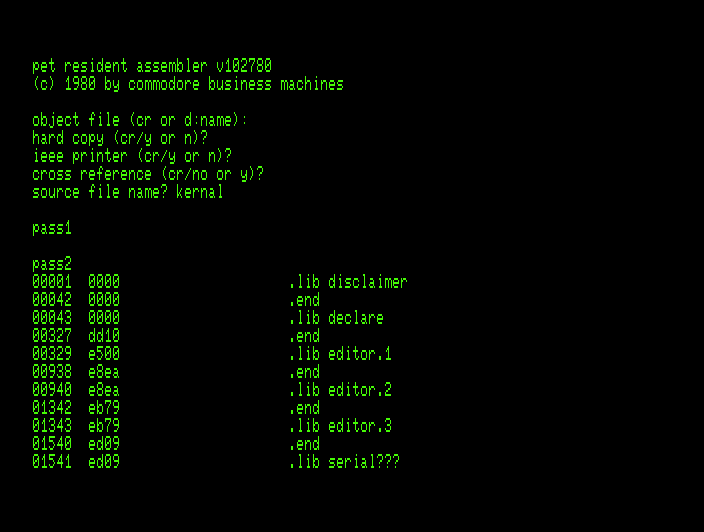
In the series about the assemblers Commodore used for developing the ROMs of their 8-bit computers, this article covers the 1976 “MOS Resident Assembler” that ran on a variety of 6502-based computers.
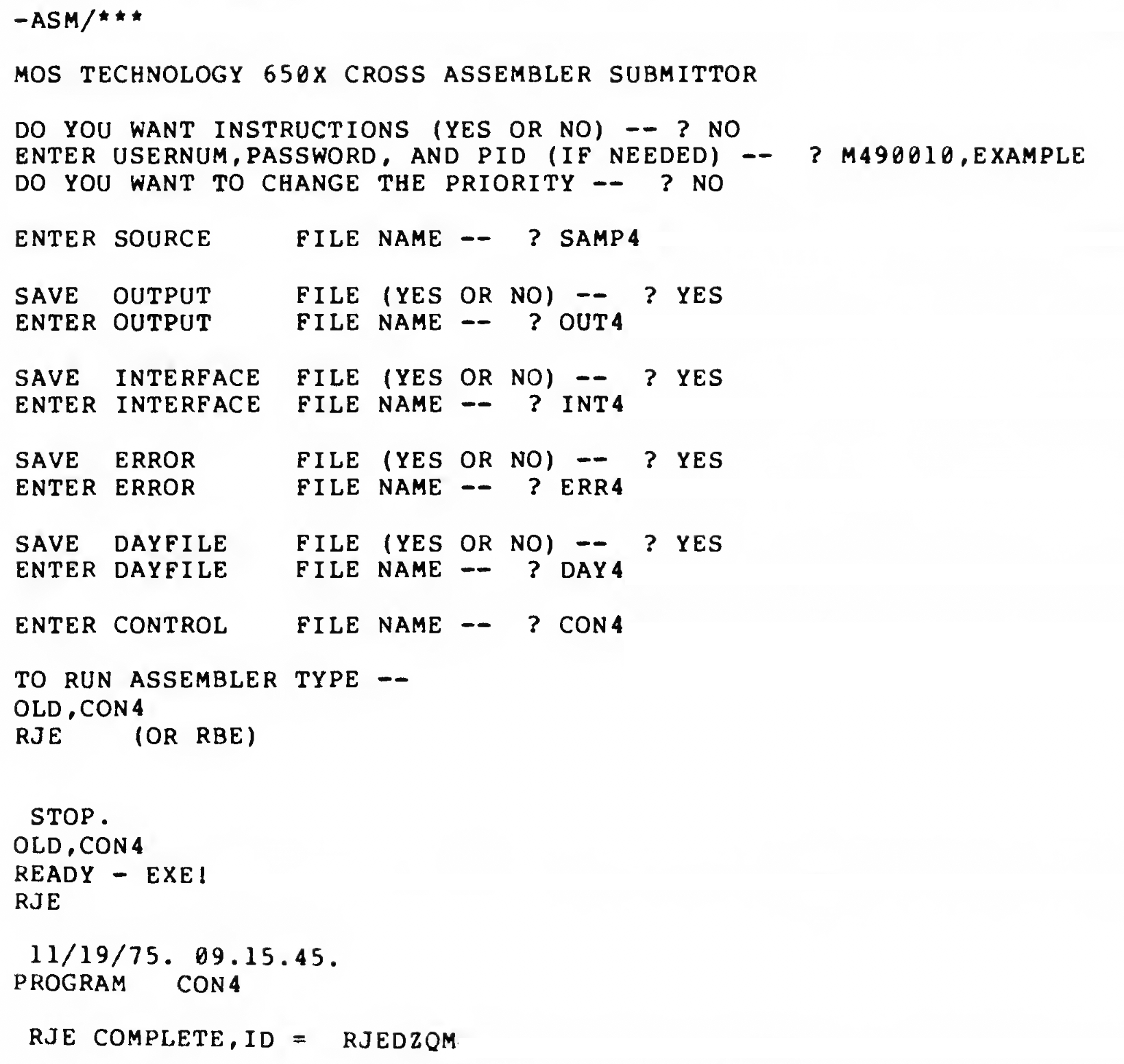
Commodore's Assemblers: Part 1: MOS Cross-Assembler
Commodore's Assemblers: Overview

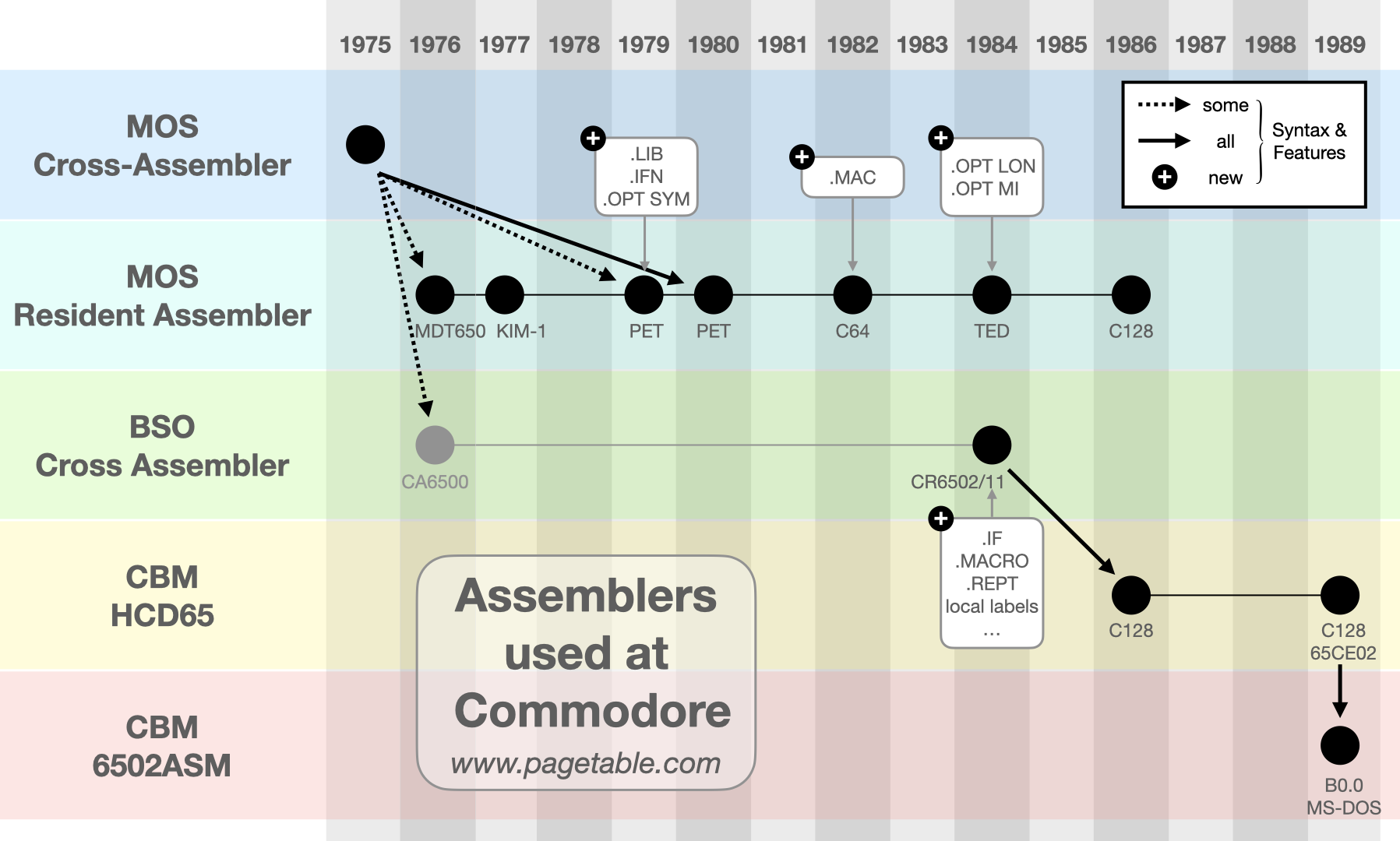
Commodore used 5 different assemblers, most of them in-house tools, to build the ROMs for their Computers like the PET, the C64 and the C128. Nevertheless, all Commodore source files, from 1975 to 1990, share a common format and use the same assembly directives. This series of articles describes each of these assemblers.
Reverse-Engineered geoWrite 2.1 for C64 Source Code
geoWrite is a WYSIWYG rich text editor for the Commodore 64 GEOS operating system. I created a reverse-engineered source version of the geoWrite 2.1 for the C64 (English and German) for the cc65 compiler suite:
Ankündigung: Vortrag "Diskettenlaufwerke am Beispiel der Commodore 1541" am VCFB 2020

This post is about an upcoming talk in German.
Inside geoWrite – 9: Keyboard Handling

In the series about the internals of the geoWrite WYSIWYG text editor for the C64, this article discusses how the app consolidates keyboard input to keep up with fast typists.
Inside geoWrite – 8: Copy & Paste
In the series about the internals of the geoWrite WYSIWYG text editor for the C64, this article discusses its efficient cross-application cut/copy/paste implementation.
Inside geoWrite – 7: File Format and Pagination
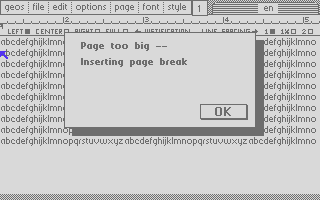
In the series about the internals of the geoWrite WYSIWYG text editor for the C64, this article discusses how its file format allows the app to efficiently edit documents hundreds of KB in size.
Inside geoWrite – 6: Localization
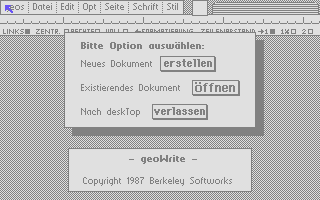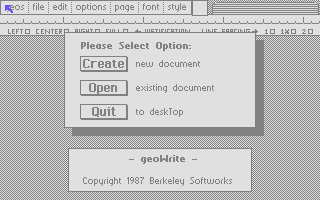
In the series about the internals of the geoWrite WYSIWYG text editor for the C64, this article discusses what was required for the German localization.
Inside geoWrite – 5: Copy Protection
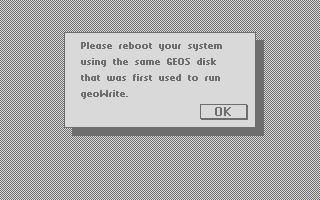
In the series about the internals of the geoWrite WYSIWYG text editor for the C64, this article discusses the geoWrite copy protection.
Inside geoWrite – 4: Zero Page
In the series about the internals of the geoWrite WYSIWYG text editor for the C64, this article discusses how it makes maximum use of the scarce zero page space.
Inside geoWrite – 3: Font Management
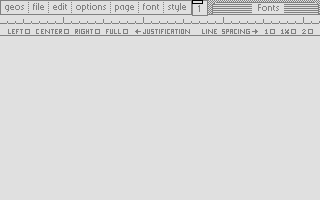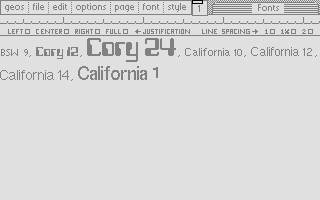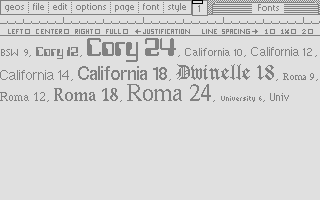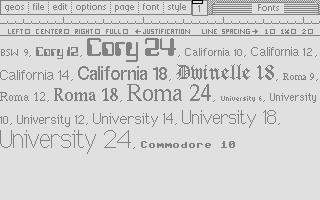
In the series about the internals of the geoWrite WYSIWYG text editor for the C64, this article discusses the font manager’s system of caches for pixel fonts.
Inside geoWrite – 2: Screen Recovery

In the series about the internals of the geoWrite WYSIWYG text editor for the C64, this article discusses how the app manages to extend its usable RAM by 5 KB using a custom screen recovery solution.
Inside geoWrite – 1: The Overlay System

geoWrite is a WYSIWYG rich text editor for the Commodore 64 GEOS operating system, which runs with a total of just 64 KB of RAM. In the series about the internals of geoWrite, this article discusses how it manages to fit 52 KB of code into the available 23 KB of application RAM.
CMDR-DOS: Commodore DOS on FAT32

All disk drives connected to the Serial Bus of a Commodore 64 speak the Commodore DOS protocol, from the popular 1541 5.25″ drive to the modern sd2iec SD card interfaces. CMDR-DOS is a new and open source implementation of the Commodore DOS protocol, using SD cards with the FAT32 filesystem and supporting advances features like partitions, subdirectories and timestamps – and running on a 65c02!
FAT32 Filesystem for the 65c02
We are presenting the (to our knowledge) first full-featured open source library for 65c02 CPUs for accessing FAT32 formatted disks.