UP9600: How to Bit-Bang 9600 Baud RS-232 on the C64
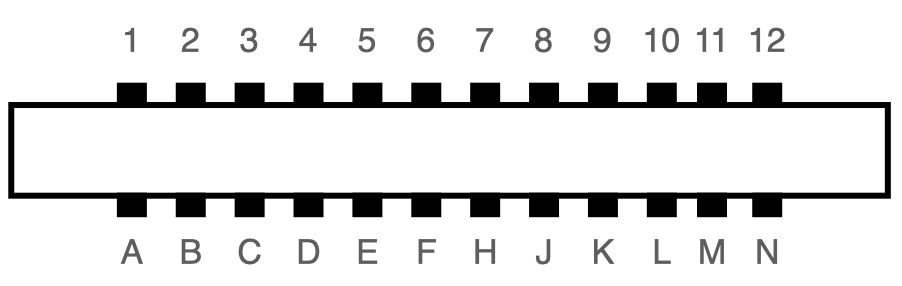
The user port of the Commodore 64 exposes a TTL-level RS-232 serial port that supports up to 1200 baud1. In 1997, Daniel Dallmann came up with a very sophisticated trick that allowed sending and receiving at 9600 baud2, using slightly different wiring and a dedicated driver. This “UP9600” wiring has become the de-facto standard for all modern accessories, like C64 WiFi modems. Let’s see how UP9600 works.
Dumping MiniDisc Media
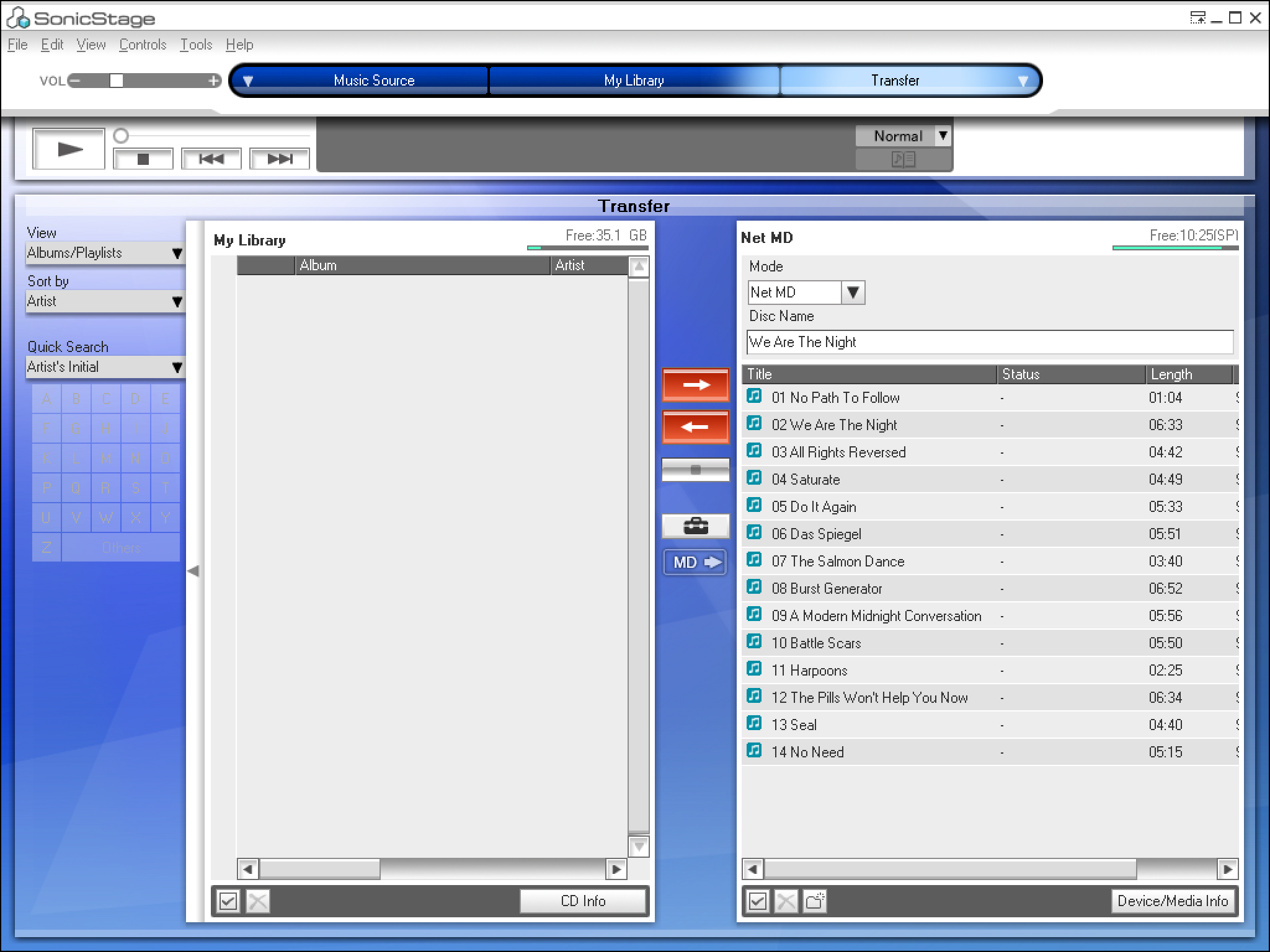
Update 2022: Web MiniDisc Pro can access NetMD devices through the browser and can also download protected files!
Commodore 64 BASIC inside your USB Connector
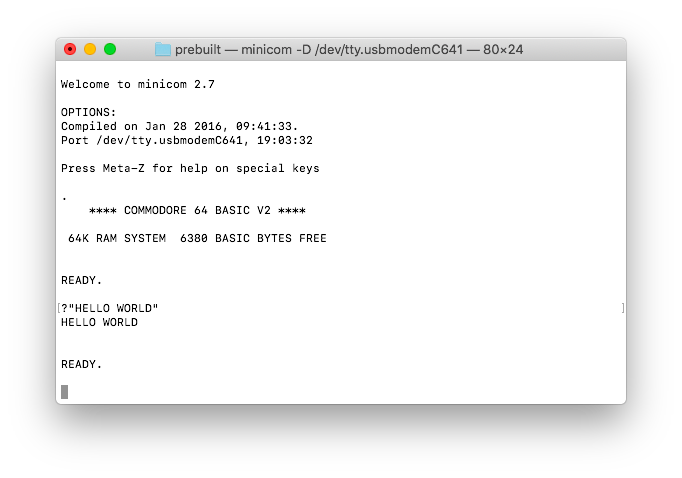
Tomu is a super cheap Open Source Hardware 24 MHz ARM computer with 8 KB of RAM and 64 KB of ROM that fits into your USB connector! Of course I had to put Commodore 64 BASIC on it, which can be accessed through the USB-Serial port exposed by the device.
Copy Protection Traps in GEOS for C64
Major GEOS applications on the Commodore 64 protect themselves from unauthorized duplication by keying themselves to the operating system's serial number. To avoid tampering with this mechanism, the system contains some elaborate traps, which will be discussed in this article.
Wikileaks Movie “The Fifth Estate” pirated my “Xbox Hacking” Slides
Chaosradio Express #177: Commodore 64
Oops! I don't have my CashCard here.
It seems that a lot of readers of pagetable.com are fans of SCUMM games like Maniac Mansion (and at least one is their creator). Here is a puzzle for you (credits go to Bernhard Bauer):
How to not get sued by Sony
Reverse Engineering the MOS 6502 CPU [video]
Here is the video recording of my presentation “Reverse Engineering the MOS 6502 CPU” given at 27C3, on the low cost CPU that arguably launched the home computer revolution.
Reverse Engineering the MOS 6502 CPU [announcement]
Xbox Serial Number Statistics
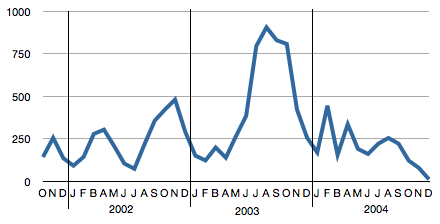
Slashdot had a story recently on how in 1942, the allies were able to estimate the number of German taks produced based on the serial numbers of the tanks. In 2010, a German hacker is doing the exact same thing with Xboxes. This article describes the generic approach, shows some results, and provides previously unreleased raw data of 14,000 Xbox serials so you can do your own statistics!
Emu8080: an HTML5 App to Emulate a Complete CP/M Machine
by Stefan Tramm
For Lisa, the World Ended in 1995
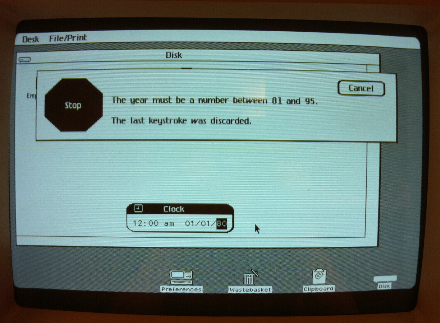
If you try to set the clock in Lisa OS 3.1 to 2010, you’re out of luck:
Internals of BRK/IRQ/NMI/RESET on a MOS 6502
After 35 years of measuring the behaviour of the MOS 6502 CPU to better understand what is going on, the Visual6502 simulator finally allows us insight into the chip, so we can understand what the CPU does internally. One interesting thing here is the question how the 6502 handles BRK, IRQ, NMI and RESET.
Playstation 3 Hacking – Linux Is Inevitable
In the talk “Why Silicon Security is still that hard” by Felix Domke at the 24th Chaos Communication Congress in 2007 (in which he described how he hacked the Xbox 360, and bushing had a cameo at the end explaining how they hacked the Wii), I had a little part, in which I argued that “Linux Is Inevitable”: If you lock down a system, it will eventually get hacked. In the light of the recent events happening with PlayStation 3 hacking, let’s revisit them.
How much change is in a vending machine?

There is only one way to find out – all you need is a giant pile of money and a vending machine that sells soda for $1.25: If you put in a dollar note and press the “return change” button, you will get the dollar note back directly. If you put in two dollar notes (the maximum it takes) at a time, it will give you change for the two dollars.
Michael Steil rocks
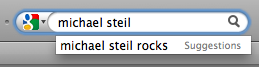
Google is always right.
TI-99/4A BASIC as a Scripting Language
It is a good time for statically recompiled versions of BASIC from old computers. First there was Apple I BASIC. Then came Commodore BASIC. Now, due to overwhelming demand, we’re proud to release TI-99/4A BASIC. For those unfamiliar the TI-99/4A was a home computer by Texas Instruments released in 1981. Unusually for the time it had a 16-bit CPU: the TMS9900.
Dangerous Xbox 360 Update Killing Homebrew
On Tuesday, Microsoft has released an Xbox 360 software update that overwrites the first stage bootloader of the system. Although there have been numerous software updates for Microsoft’s gaming console in the past, this is the first one to overwrite the vital boot block. Any failure while updating this will break the Xbox 360 beyond repair. Statistics from other systems have shown that about one in a thousand bootloader updates goes wrong, and unless Microsoft has a novel solution to this problem, this puts tens of thousands of Xboxes at risk.
Stamp Vending Machine DoS
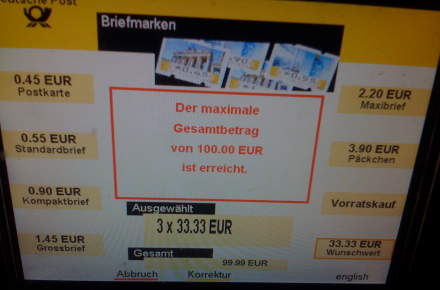
It makes sense for a stamp vending machine to have some limits and not print any amount of stamps or stamps of any value. The vending machines from the Deutsche Post are a little weird though:




